 In this post, you will learn about listing users in Linux. Besides this, you will know other tricks about Linux users’ characteristics. There are 2 types of users in Linux, system users who are created by default with the system. On the other hand, there are regular users who are created by system administrators and can log in to the system and use it. Before we start listing users, we need to know where are these users saved on Linux? The users are stored in a text file on the system called the passwd file. This file is located in the /etc directory. The file is located on the following path:
In this post, you will learn about listing users in Linux. Besides this, you will know other tricks about Linux users’ characteristics. There are 2 types of users in Linux, system users who are created by default with the system. On the other hand, there are regular users who are created by system administrators and can log in to the system and use it. Before we start listing users, we need to know where are these users saved on Linux? The users are stored in a text file on the system called the passwd file. This file is located in the /etc directory. The file is located on the following path:
/etc/passwd
In this file, you can find all the information about the users in the system.
List all users
Listing users is a the first step to manage them. This way we will know how many they are and who they are. In Linux, almost everything can be done in various ways and this is no exception.
To list all users, you can use the cat command:
cat /etc/passwd
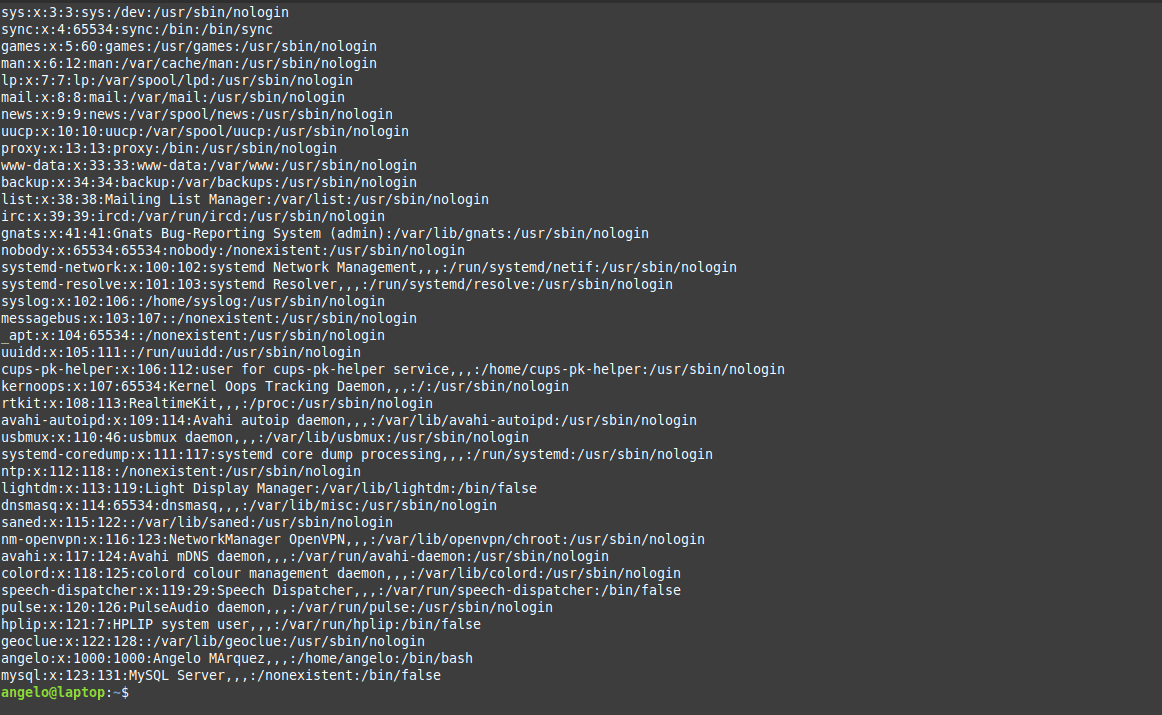
As you can see in the image, there is all the information about the users.
1- In the first field, you will see the user name.
2- Then, a representation of the encrypted password (The x character). The encrypted password is stored in /etc/shadow file.
3- The UID or the user ID.
4- The next field refers to the primary group of the user.
5- Then, it shows user ID info such as the address, email, etc.
6- After this, you will see the home directory of the user.
7- The last field is the shell used by that user.
However, although the information is quite useful but if you only want to list users’ names in a basic way, you can use this command:
cut -d: -f1 /etc/passwd
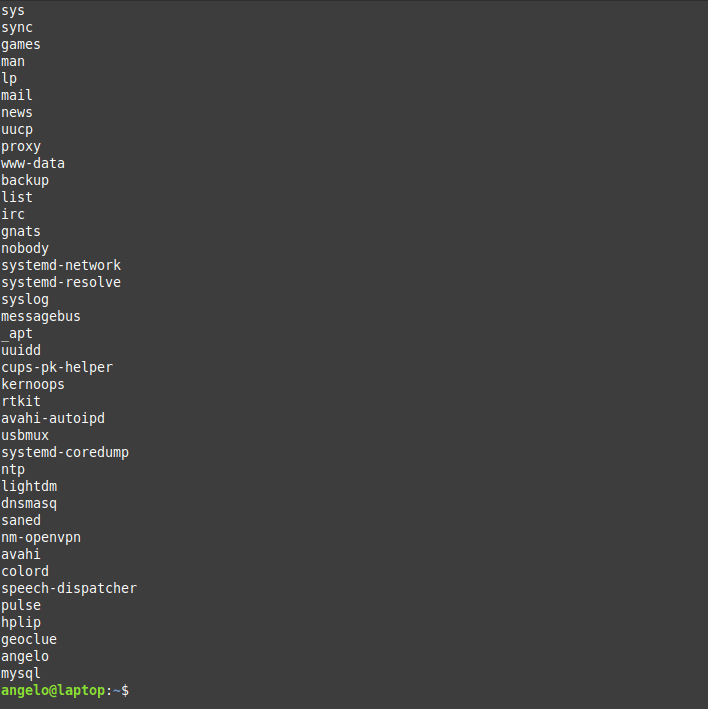
Now we have the names only by printing the first field of te file only.
List & sort users by name
The above command serves the purpose of listing users on Linux. But what about listing the users in alphabetical order?
To do this, we will use the previous command, but we will add the sort command.
So, the command will be like this:
cut -d: -f1 /etc/passwd | sort
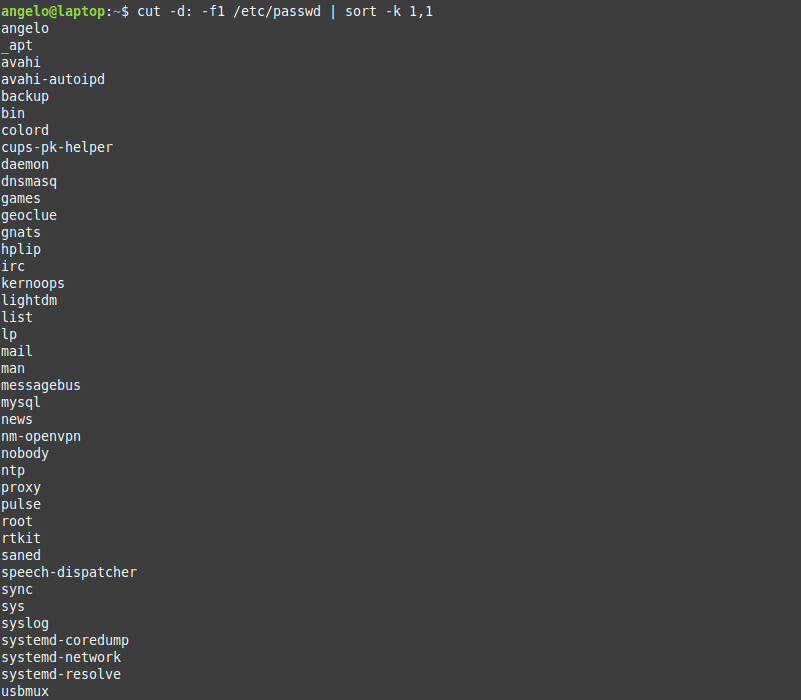
As you can see in the image, the users are shown sorted.
Linux list users without password
It is important to know users who have no password and to take appropriate action. To list users who do not have a password, just use the following command:
sudo getent shadow | grep -Po '^[^:]*(?=:.?:)'
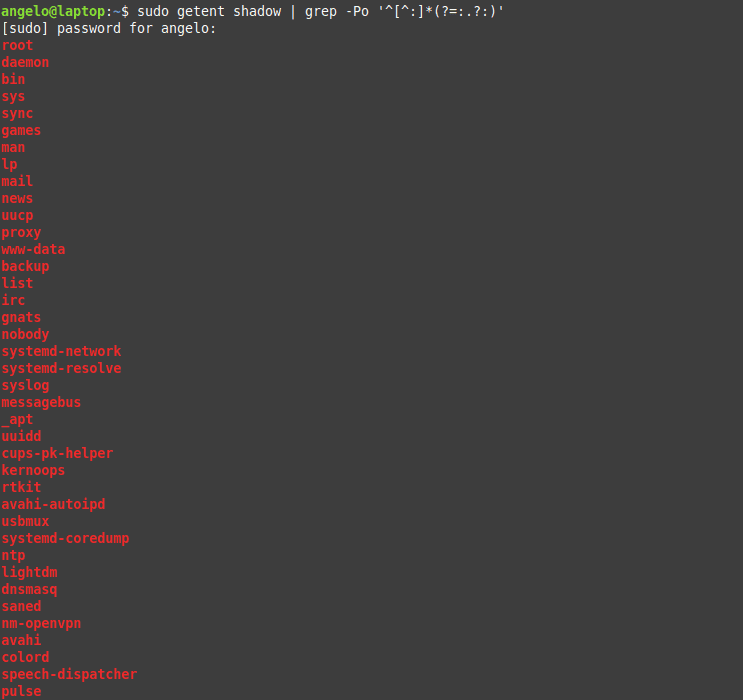
The used regex will list all users with no password.
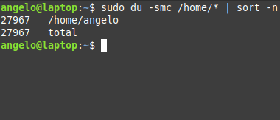
List users by disk usage
If you have a big directory and you want to know which user is flooding it, you can use the du command to get the disk usage.
With this, you can detect which of these users are misusing the disk space.
For it, it is enough to use the following command:
sudo du -smc /home/* | sort -n
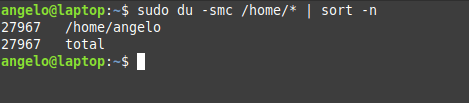
In this way, you will have the users ordered by the disk usage for the /home directory.
We used the -n for the sort command to sort the output by numbers.
List the currently logged users
To list the currently logged in users, we have several ways to do it. The first method we can use the users command:
users
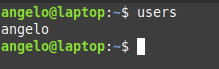
It will list the users with open sessions in the system.
But this information is a little basic however, we have another command that gives more details. The command is simply w.
w
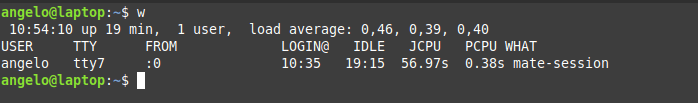
With this command, we can have more information such as the exact time when the session was started and the terminal session he has available.
Finally, there is a command called who. It is available to the entire Unix family. So you can use it on other systems like FreeBSD.
who
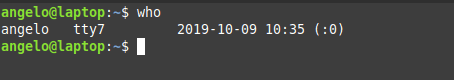
With who command, we also have some information about currently logged in users. Of course, we can add the option -a and show all the details.
who -a
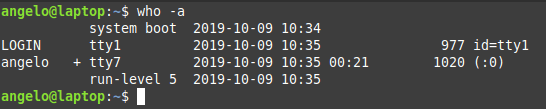
So, this way you know everything about the logged in users.
Linux list of users who recently logged into the system
We saw how to get the currently logged in users, what about listing the login history of users?
You can use the last command to get more info about the logins that took place:
last
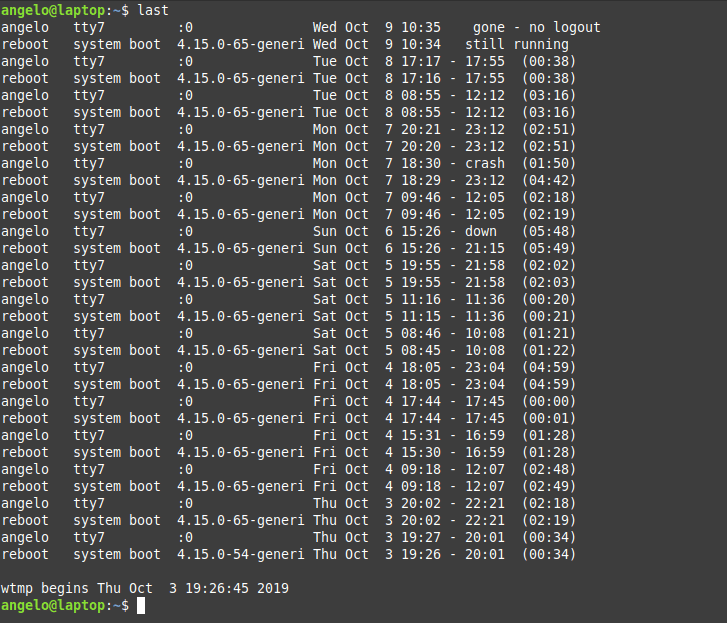
Or the logins of a particular user
last [username]
For example:
last angelo
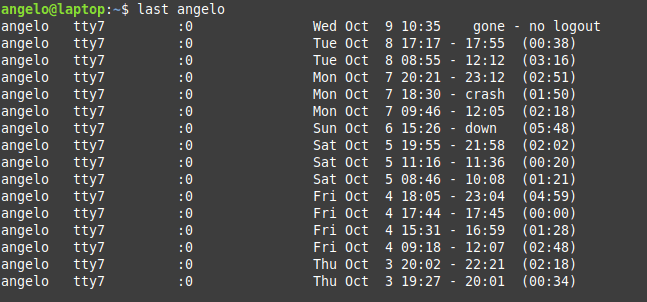
These are the user login activity and when it was started and how long it took.
List users’ logins on a specific date or time
What about listing users’ logins on a specific date or time? To achieve this, we use the last command but with the -t parameter:
last -t YYMMDDHHMMSS
For example:
last -t 20190926110509
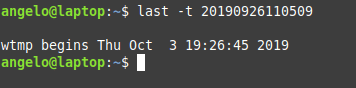
And now all you have to do is choose an exact date & time to list who logged on that time.
List all users in a group
There are 2 ways to list the members of a group in Linux, the easiest and most direct way is to get the users from the /etc/group file like this:
cat /etc/group | grep likegeeks
This command will list users in the likegeeks group.
The other way is by using commands like the members command in Debian based distros. However, it is not installed by default in Linux distributions.
To install it in Ubuntu / Linux Mint 19, just use APT:
sudo apt install members
Or in the case of CentOS:
sudo dnf install members
Once it’s installed, you can run the command then the name of the group you want to list the users to:
members [group_name]
For example:
members avahi
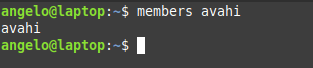
This way you can list users for a group in a Debian based distro. What about a RedHat based distro like CentOS?
You can use the following command:
getent group likegeeks
List users with UID
In Unix systems, each user has a user identifier or ID. It serves to manage and administer accounts internally in the operating system.
Generally, UIDs from 0 to 1000 are for system users. And thereafter for regular users. Always on Unix systems, UID zero belongs to the root users (You can have more than one user with UID of zero).
So now we will list the users with their respective UID using awk.
The command that performs the task is the following:
awk -F: '{printf "%s:%s\n",$1,$3}' /etc/passwd
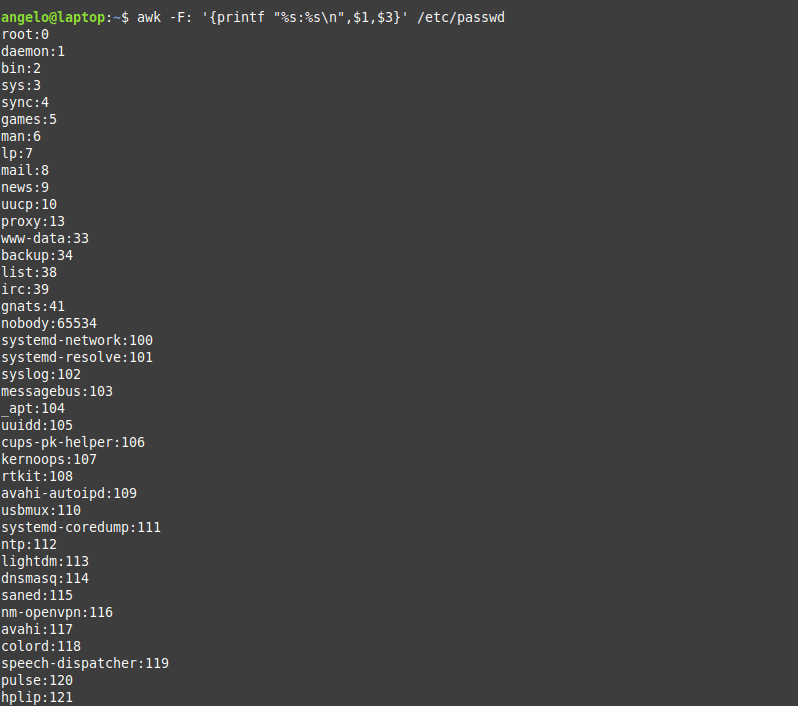
As you can see, each user with his UID.
List root users
In a Unix-like system like Linux, there is usually only one root user. If there are many, how to list them?
To do this, we can use this command:
grep 'x:0:' /etc/passwd
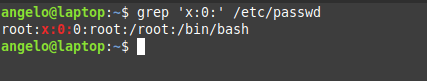
Here we are filtering the file to get users with UID of zero (root users).
Another way by checking the /etc/group file:
grep root /etc/group
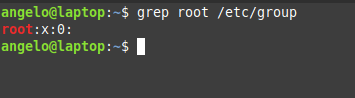
Here we are getting users in the group root from the /etc/group file.
Also, you can check if any user can execute commands as root by checking the /etc/sudoers file:
cat /etc/sudoers
Get the total number of users
To get the total number of users in Linux, you can count lines in /etc/passwd file using the wc command like this:
cut -d: -f1 /etc/passwd | wc -l
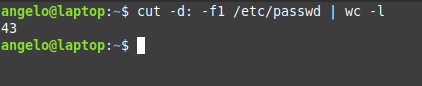
Great! 43 users. But this includes system and regular users. What about getting the number of regular users only?
Easy! Since we know from above that regular users have UID of 1000 or greater, we can use awk to get them:
awk -F: '$3 >= 1000 {print $1}' /etc/passwd
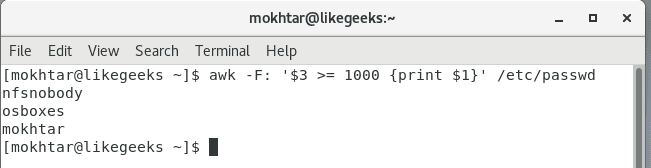
Cool!
List sudo users
Linux systems have a utility called sudo that allows you to execute commands as if you were another user who is usually the root user.
This should be handled with care in a professional environment.
Also, it is very important to know which users can run the sudo command. For this, it is enough to list the users that belong to the sudo group.
members sudo
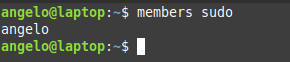
Users in this group can execute commands as super users.
List users who have SSH access
SSH allows users to access remote computers over a network. It is quite secure and was born as a replacement for Telnet.
On Linux by default, all regular users can log in and use SSH. If you want to limit this, you can use the SSH configuration file (/etc/ssh/ssh_config) and add the following directive:
AllowUsers user1 user2 user3
Also, you can allow groups instead of allowing users only using the AllowGroups directive:
AllowGroups group1 group2 group3
These directives define who can access the service. Don’t forget to restart the SSH service.
List users who have permissions to a file or directory
We can give more than one user permission to access or modify files & directories in two ways.
The first method is by adding users to the group of the file or the directory.
This way, we can list the group members using the members utility as shown above.
Okay, but what if we just want this user to have access to this specific file only (Not all the group permissions)?
Here we can set the ACL for this file using setfacl command like this:
setfacl -m u:newuser:rwx myfile
Here we give the user called newser the permission for the file called myfile the permissions of read & write & execute.
Now the file can be accessed or modified by the owner and the user called newuser. So how to list them?
We can list them using the getfacl command like this:
getfacl myfile
This command will list all users who have permissions for the file with their corresponding permissions.
List locked (disabled) users
In Linux, as a security measure, we can lock users. This as a precaution if it is suspected that the user is doing things wrong and you don’t want to completely remove the user and just lock him for investigation.
To lock a user, you can use the following command:
usermod -L myuser
Now the user named myuser will no longer to able to login or use the system.
To list all locked users of the system, just use the following command:
cat /etc/passwd | cut -d : -f 1 | awk '{ system("passwd -S " $0) }' | grep locked
This will print all locked users including system users. What about listing regular users only?
As we saw above, using awk we can get locked regular users like this:
awk -F: '$3 >= 1000 {print $1}' /etc/passwd | cut -d : -f 1 | awk '{ system("passwd -S " $0) }' | grep locked
Very easy!
Listing remote users (LDAP)
Okay, now can list all system users (local users), but what about remote users or LDAP users? Well, we can use a tool like ldapsearch, but is there any other way?
Luckily yes! You can list local & remote users with one command called getent
getent passwd
This command lists both local system users and LDAP or NIS users or any other network users.
You can pipe the results of this command to any of the above-mentioned commands the same way.
Also, the getent command can list group accounts like this:
getent group
You can check the man page of the command to know the other databases the command can search in.
Conclusion
Listing users in the Linux system was fun! Besides this, we have learned some tips about users and how to manage them in different ways.
Finally, this knowledge will allow a better administration of the users of the system.
I hope you find the tutorial useful. keep coming back.



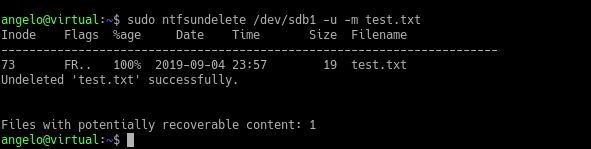
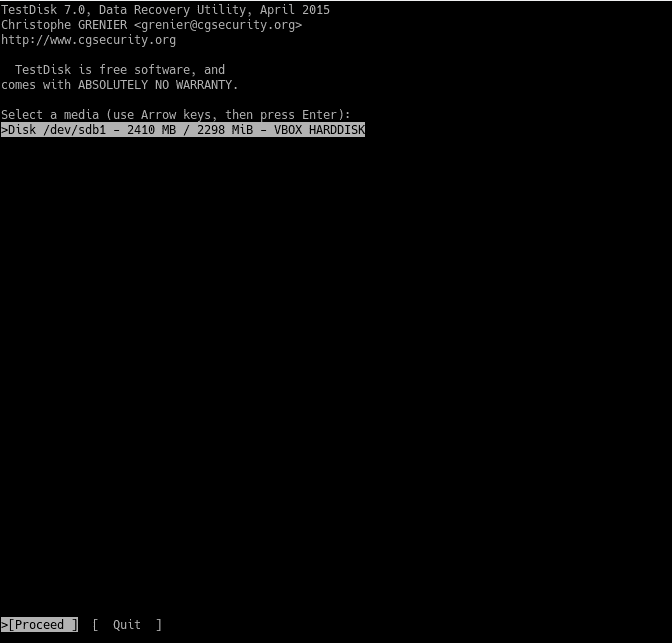
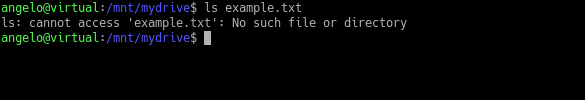
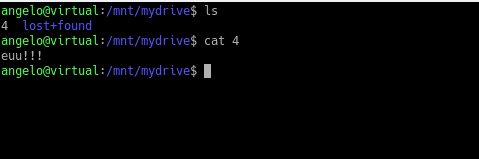
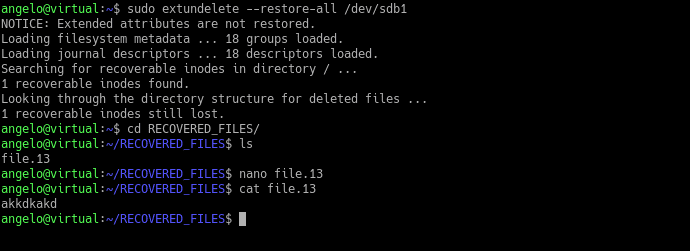
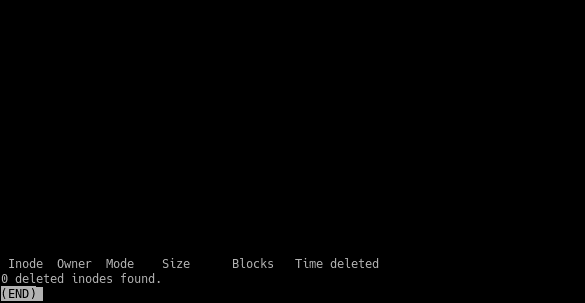
 Have you ever deleted any important files by mistake? Who doesn’t! Okay, but can I recover them? In this post, you will learn how to recover deleted files on
Have you ever deleted any important files by mistake? Who doesn’t! Okay, but can I recover them? In this post, you will learn how to recover deleted files on 

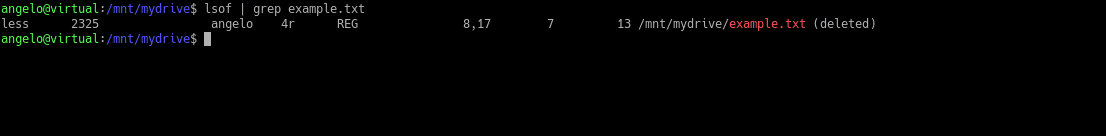
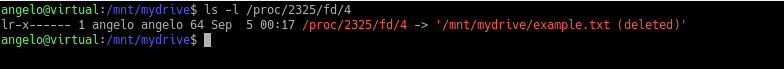

 If you want to process large files using PHP, you may use some of the ordinary PHP functions like file_get_contents() or file() which has a limitation when working with very large files. These functions rely on the memory_limit setting in php.ini file, you may increase the value but these functions still are not suitable for very large files because these functions will put the entire file content into memory at one point. Any file that has a size larger than memory_limit setting will not be loaded into memory, so what if you have 20 GB file and you want to process it using PHP? Another limitation is the speed of producing output. Let’s assume that you will accumulate the output in an array then output it at once which gives a bad user experience. For this limitation, we can use the yield keyword to generate an immediate result.
If you want to process large files using PHP, you may use some of the ordinary PHP functions like file_get_contents() or file() which has a limitation when working with very large files. These functions rely on the memory_limit setting in php.ini file, you may increase the value but these functions still are not suitable for very large files because these functions will put the entire file content into memory at one point. Any file that has a size larger than memory_limit setting will not be loaded into memory, so what if you have 20 GB file and you want to process it using PHP? Another limitation is the speed of producing output. Let’s assume that you will accumulate the output in an array then output it at once which gives a bad user experience. For this limitation, we can use the yield keyword to generate an immediate result.