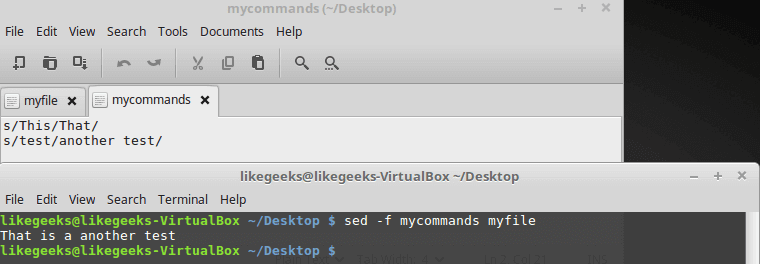
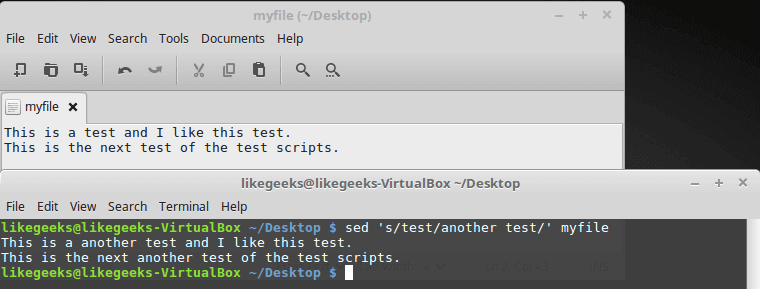
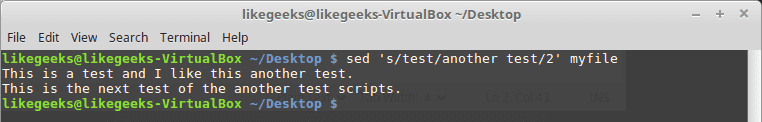
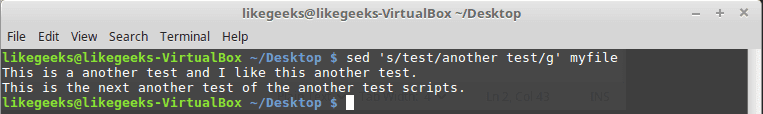
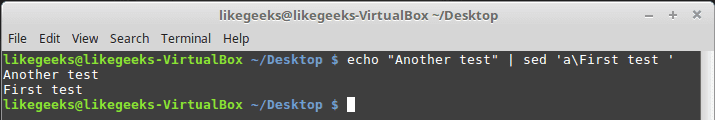
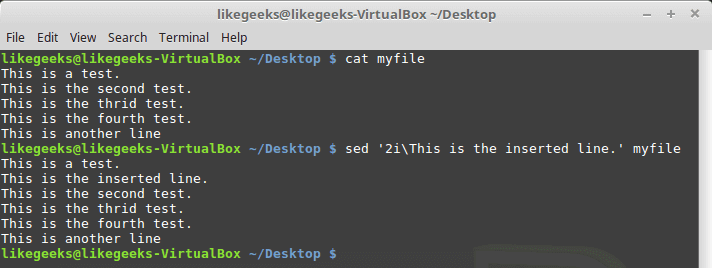
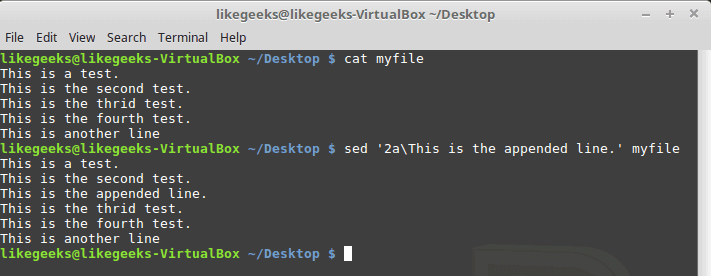
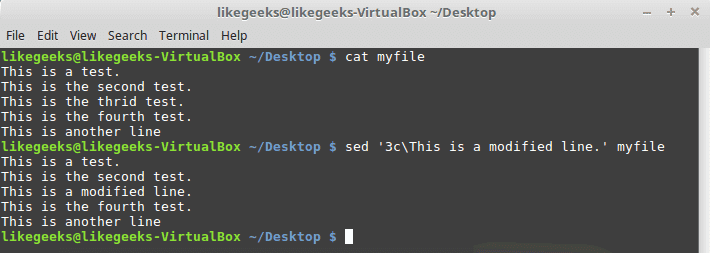
Hackers can access, steal and sell your online activity data as well as manipulate it if you don’t use the right system and tools. The level of protection you want will largely influence which tools and systems to use. With a Linux system and VPN, it becomes possible to hide your browsing tracks, personal information, and various other online activities. When you have the right protection in place, not even the government can access your activity. Keep reading to learn how businesses and individuals alike can use a Linux system and VPN for ongoing protection of their online data. We will also explore why this is important and why you should care about your online data. Hackers steal data for a number of reasons. Sometimes, it’s’ for their own purposes. Other times, they sell it or give it to other entities. These entities may or may not have known about the data collection processes the hackers use to gather the data.
Hackers can access, steal and sell your online activity data as well as manipulate it if you don’t use the right system and tools. The level of protection you want will largely influence which tools and systems to use. With a Linux system and VPN, it becomes possible to hide your browsing tracks, personal information, and various other online activities. When you have the right protection in place, not even the government can access your activity. Keep reading to learn how businesses and individuals alike can use a Linux system and VPN for ongoing protection of their online data. We will also explore why this is important and why you should care about your online data. Hackers steal data for a number of reasons. Sometimes, it’s’ for their own purposes. Other times, they sell it or give it to other entities. These entities may or may not have known about the data collection processes the hackers use to gather the data.
What Is a VPN?
VPN stands for virtual private network, which means it provides encryption, making it difficult for the bad guys to steal your data when visiting their sites. It also acts as an added layer of protection against the government from tracking your online activity.
In some areas, a VPN even grants users access to certain content that is not normally available in their geographical areas. Such forms of content often include video, international gaming, certain servers, etc.
The VPN works to protect your online activity by making it appear as if you are logged in from a different location. As soon as you connect to the VPN, you can set your location to anywhere in the world.
Additionally, with a Linux system, you can improve the safety and protection of your data thanks to advanced security measures. Fixes for Linux program exploits made by hackers are generally developed and released well before other operating systems develop and release fixes for their equivalent programs.
How Does a Linux System Make Online Activity More Secure?
Getting fixes to exploits is of the utmost importance in both personal and business settings, particularly those sitting on large amounts of data.
Hackers, crackers, and phreakers steal people’s online data all the time for multiple reasons. Some do it to fight a cause, some steal it unintentionally, some do it for fun, a few do it for commercial espionage or sabotage, and lastly, it’s not uncommon for disgruntled employees to steal data for whistle blowing purposes.
A Linux system helps avoid several types of attacks:
- Reading data
- Denial of service
- Altering/manipulating data
- Access to system
Tips for Increasing Data Protection With a Linux System
To increase data protection through the use of a Linux system, you must first pinpoint what you mean by “secure.” To do this, you must assess what you intend to do with the system and just how secure you need the data to be. In most cases, Linux systems need security, at a minimum, in the following areas:
- Authorization: Do not allow ANYONE access to the system unless they NEED access
- Verification: Make sure users have to go through a 2-step authentication process to verify their identity each time logging into the system
- Integrity: All personal information must be protected and NEVER compromised
- Non-repudiation: Must have proof of receipt of data; official receipt showing how you received the data and from whom
- Privacy/confidentiality: You must abide by any privacy and confidentiality regulations such as the ISO 7984-2 International Standards Organization Security Standard
- Availability: System must be able to perform its required function at all times during normal operating hours while maintaining security around the clock.
Choose a Native App
When installing a VPN on a Linux system, you will have two options: Open-source or native app. With a native app, you will get access to more features and less required configuration.
Because of this, it is highly suggested that any VPN you use at least comes in the form of a native client for Linux.
In addition to the dedicated app, users of a VPN that comes in the form of a native client enjoy sophisticated security, ultra-fast speeds, and the ability to run on a command-line interface. Additionally, the server list is always kept up to date, making it simple to download and switch between UDP to TCP over the Open VPN protocol.
Run Through Services and Customize Each of Them
When using Linux as a VPN, you will have several types of facilities to choose from, including mail and WWW. Linux handles some of these services through a system of ports.
Take for example Port 21, which controls FTP. You can check out service names in the /etc/services file for a map of port numbers.
It’s ideal to have most of your services running through a configuration file /etc/inetd.conf. You’ll also want to take a lot of time when running through this type of file as you will have the ability to customize how each of the available services is running and protected.
Keep Services in inetd.conf Turned OFF
Check the services in inetd.conf, and make sure they are not set to turn on by default. To achieve maximum security, you must turn them off. You can type the command netstat -vat to see which services are currently running on your Linux or alternatively, you can use ss command. For any services that you are unfamiliar with, make sure to look them up in /etc/inetd.conf.
Final Thoughts
There are numerous VPNs to choose from. The surfshark.com VPN is especially ideal for those who want to unblock lots of region-locked content from sources such as Netflix, Amazon Prime Video and Hulu.
Users of this VPN are also huge fans of their ability to connect to the VPN through an unlimited number of devices. This is an example of a VPN that has the features you should look for when researching for ways to use a Linux system to secure internet activity.



 In the previous post, we talked about
In the previous post, we talked about